Which Statement Describes the Best Practice for Securing a Load
Include feedback loops and communicate current operating status of the business through dashboards and Include feedback loops for procedures to. Complete your training with support from the experts.

How To Tie Various Knots Prussic Knot Best Knots Rope Knots Climbing Knots
Enter the name of the Application in the Global search field.

. When you plan to initially load a lot of data you can shorten the time it takes to populate the database by temporarily turning off full-text search and turning it on again after the export on the MIM 2016 management agent FIM MA has. Azure Machine Learning Studio gives you an interactive visual workspace to easily build test and iterate on a predictive analysis model. AWS Certified Cloud Practitioner 6 full practice tests Set 2.
Cargo that is improperly secured can cause severe accidents and lead to the loss of cargo lives and. Name Extract Transform Load ETL Best Practices Description In defining the best practices for an ETL System this document will present the requirements that should be addressed in order to develop and maintain an ETL System. Which connections use a virtual private gateway in an Amazon VPC.
Deploying multiple EBS volumes for EC2 Instances. Reducing the costs for your solution. Reduce local Administrators group membership on all AD FS servers.
This document describes the best practice and alternative scenario for deploying ASA-5500 VPN remote access solution in a Load BalancingClustering environment using digital certificates authentication. Load securing also known as cargo securing is the securing of cargo for transportation. O The collection of interface labels on physical appliances.
All of the following statements support the best practice of Prepare EXCEPT for these two responses. Groups let you specify permissions for multiple users which can make it easier to manage the permissions. For more information on VPN Load BalancingClustering High Availability services of the ASA appl.
According to the European Commission Transportation Department it has been estimated that up to 25 of accidents involving trucks can be attributable to inadequate cargo securing. The initial load of data can be a lengthy process. Which type of load balancer would most benefit websites and mobile applications that run containers on Amazon Elastic Compute Cloud Amazon EC2 instances.
Get answers to platform specific questions from Anaplanners everywhere. The SNMP ACE would be entered before the other UDP ACE. Citizenship and Immigration Services Form I-9 and providing supporting documentation.
O A set of logical connections into which EdgeConnect places traffic that matches an Interface label or access list. Step through code in a modern browser on localhost An easy way to debug code is to use a modern browsers debugger to step through code such as a module or data action that is typically run on the server side. Ensure only Active Directory Admins and AD FS Admins have admin rights to the AD FS system.
The purpose is to establish identity and employment authorization. Consider the two permit UDP statements. A best practice for configuring an extended ACL is to ensure that the most specific ACE is placed higher in the ACL.
Which of the following statements best describes the purpose of completing Department of Homeland SecurityUS. Workshop content submit for approval and contribute best practices to the Community. O The physical transport connections between appliances.
If both of these were in an ACL the SNMP ACE is more specific than the UDP statement that permits a range of 10001 UDP port numbers. CCNA 3 Practice Final Exam v50 v502 v503 v51 v60 Exam Questions Answers 2019 2020 100 Update 2017 - 2018 Latest version Scaling NetworksPDF Free Download. The following is a list of best practices and recommendations for hardening and securing your AD FS deployment.
O A list of the IP addresses applied to each appliance. Which of the below statements are valid benefits. Configure the SQL server for initial data load.
Choose 2 Enables you to attach IAM permission policies to more than one user at a time. Open the artifact records individually to verify the value in the Application field. Which of the following examples supports the cloud design principle of design for failure and nothing will fail.
These best practices will address the constraints placed on the ETL system and how best to. Microsoft Azure Machine Learning Studio is a collaborative drag-and-drop tool you can use to build test and deploy predictive analytics solutions on your data. 4Which statement best describes an overlay network.
SecDevOps sometimes called Rugged DevOps or security at speed as a set of best practices designed to help organizations implant secure coding deep in the heart of their DevOps development and deployment processesIt seeks to embed security inside the development process as deeply as DevOps has done with operations. This topic describes some best practices to follow when debugging Dynamics 365 Commerce customizations. Which statement describes what the AWS Support Concierge service provides.
Distributes load to a single server. Deploying an application across multiple availability zones. Elastic Load Balancing is managed by AWS and scales automatically.
Network Load Balancer NLB Your manager has asked you to explain the benefits of using IAM groups. The purpose is to determine tax identification and withholding. Examine the Application Files Related List in the application to be published Correct D.
Require all cloud admins use Multi-Factor Authentication MFA. Share ideas for platform improvements training the Community and more. Hardware virtual private network VPN AWS Direct Connect DX Which statement describes the purpose of simple routing with Amazon Route S3.
IT Essentials Version 700 - IT Essentials 70 Chapter 10 exam Answers full new questions v701 v60 100 scored 2021 2022 pdf file free download. A best practice is to use custom route tables for each subnet which enables granular routing for destinations.
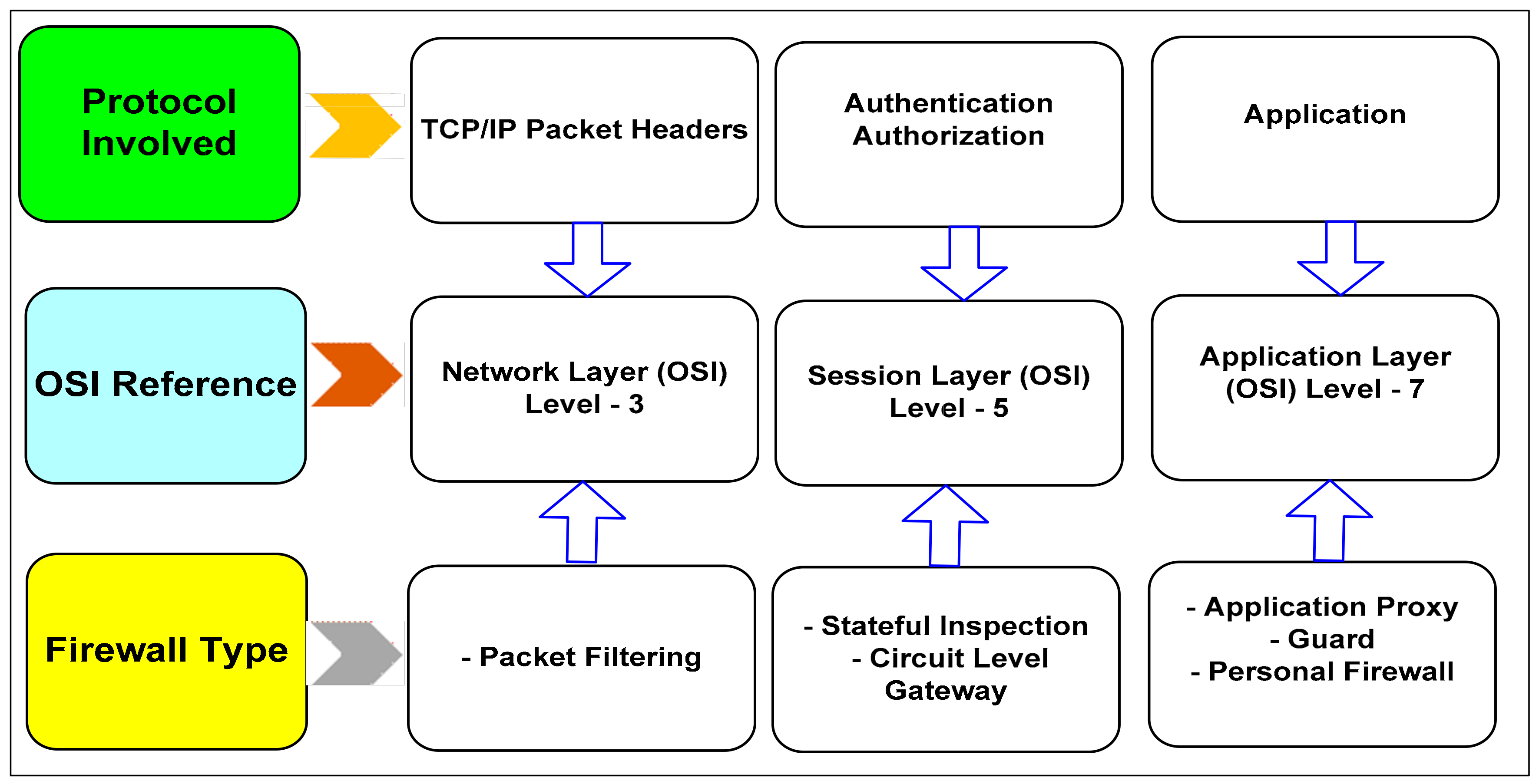
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

8 Best Practices To Improve Kubernetes Security Updated 2021 Cycode
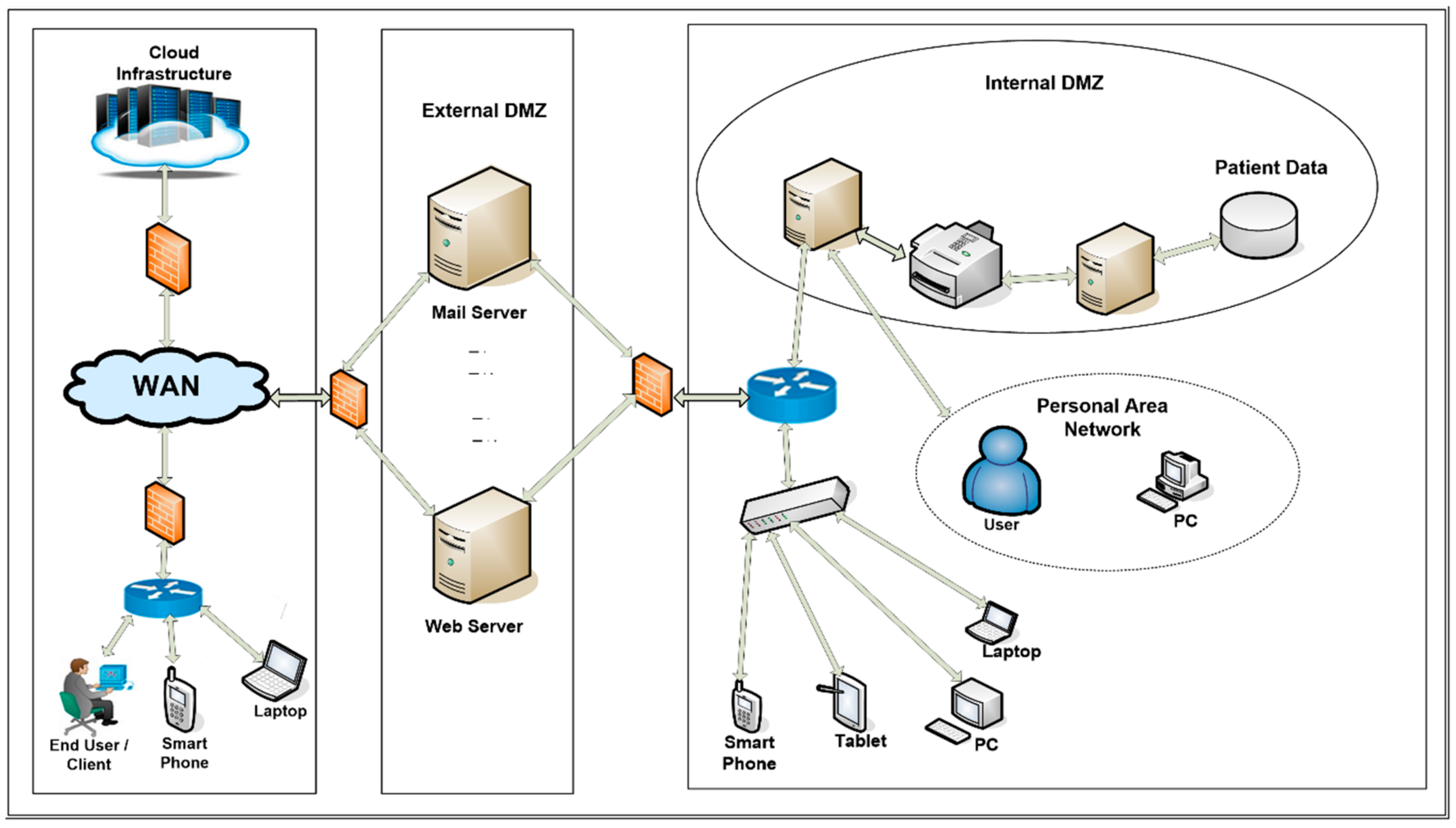
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
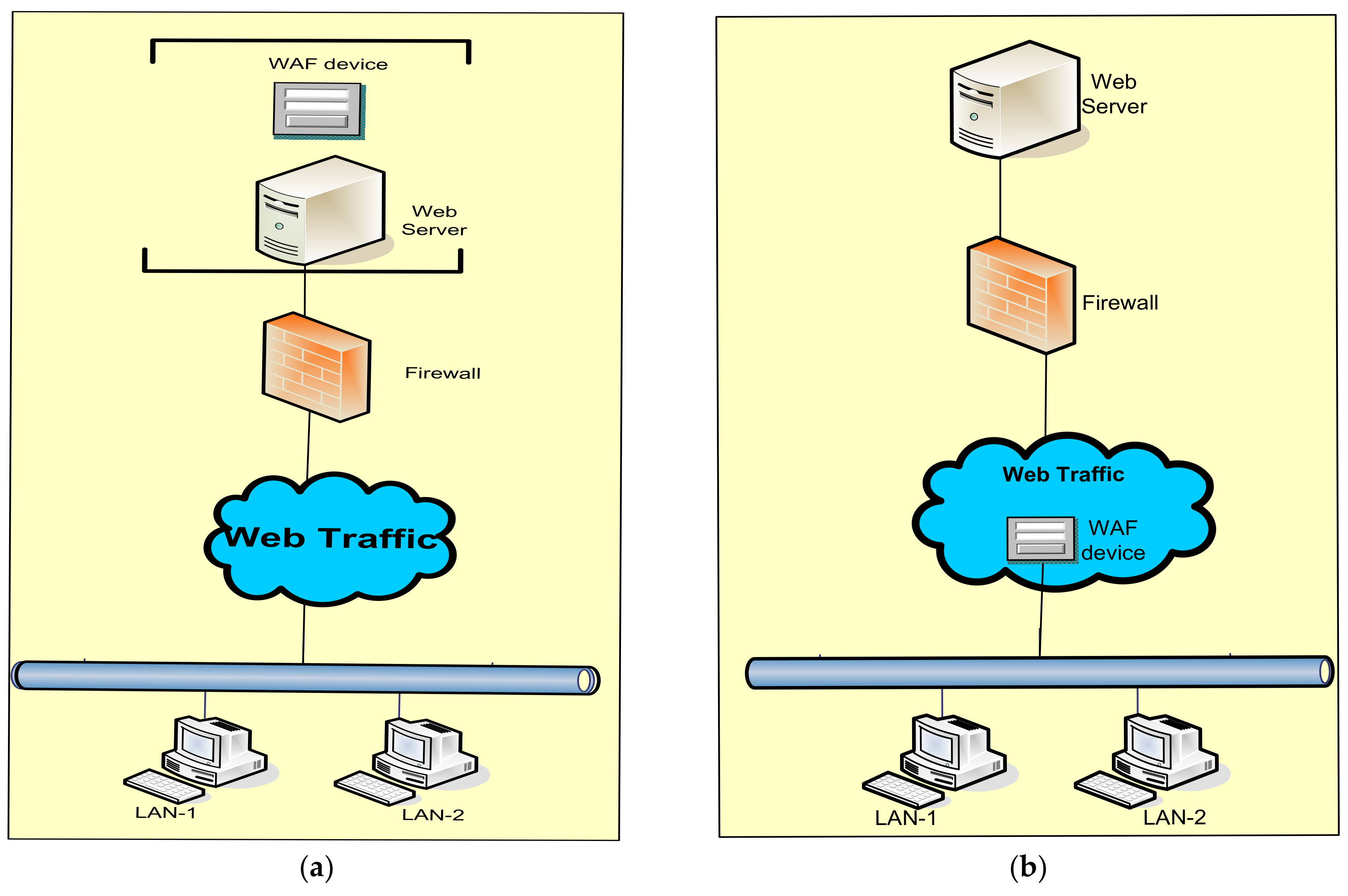
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

Best Practices For Securing Your Applications And Apis Using Apigee Data Integration

Infosec Strategies And Best Practices Packt

The Three States Of Data Guide Description And How To Secure Them

Sending Secure Email Ome Ame And Sensitivity Labels What Gives Joanne C Klein

What Is Email Encryption Methods Keys Asymmetric Rsa Security

What Is Application Security Vmware Glossary
Best Practices For Securing Your Applications And Apis Using Apigee Data Integration

Deploying Nginx As An Api Gateway Part 1 Nginx
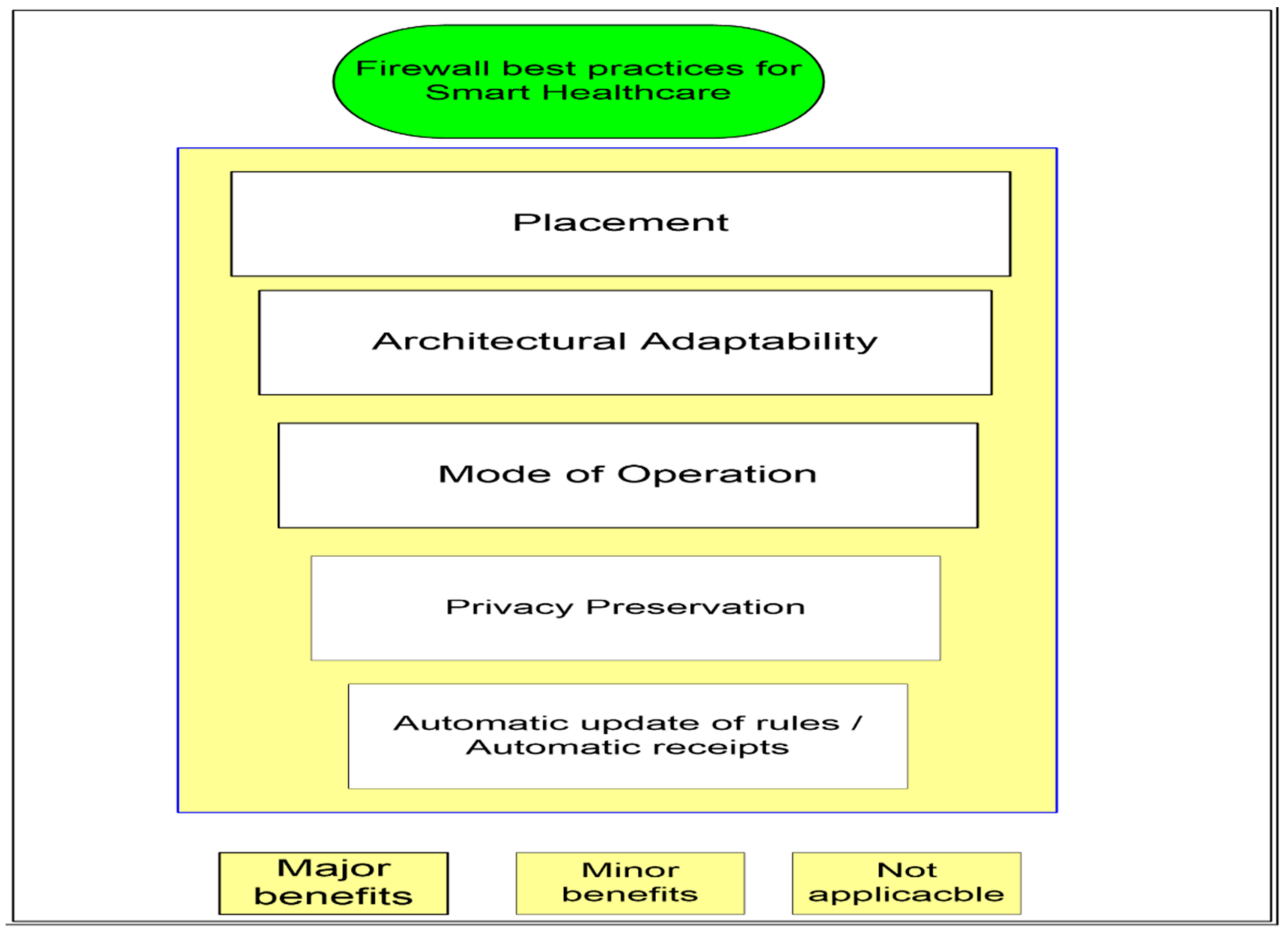
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
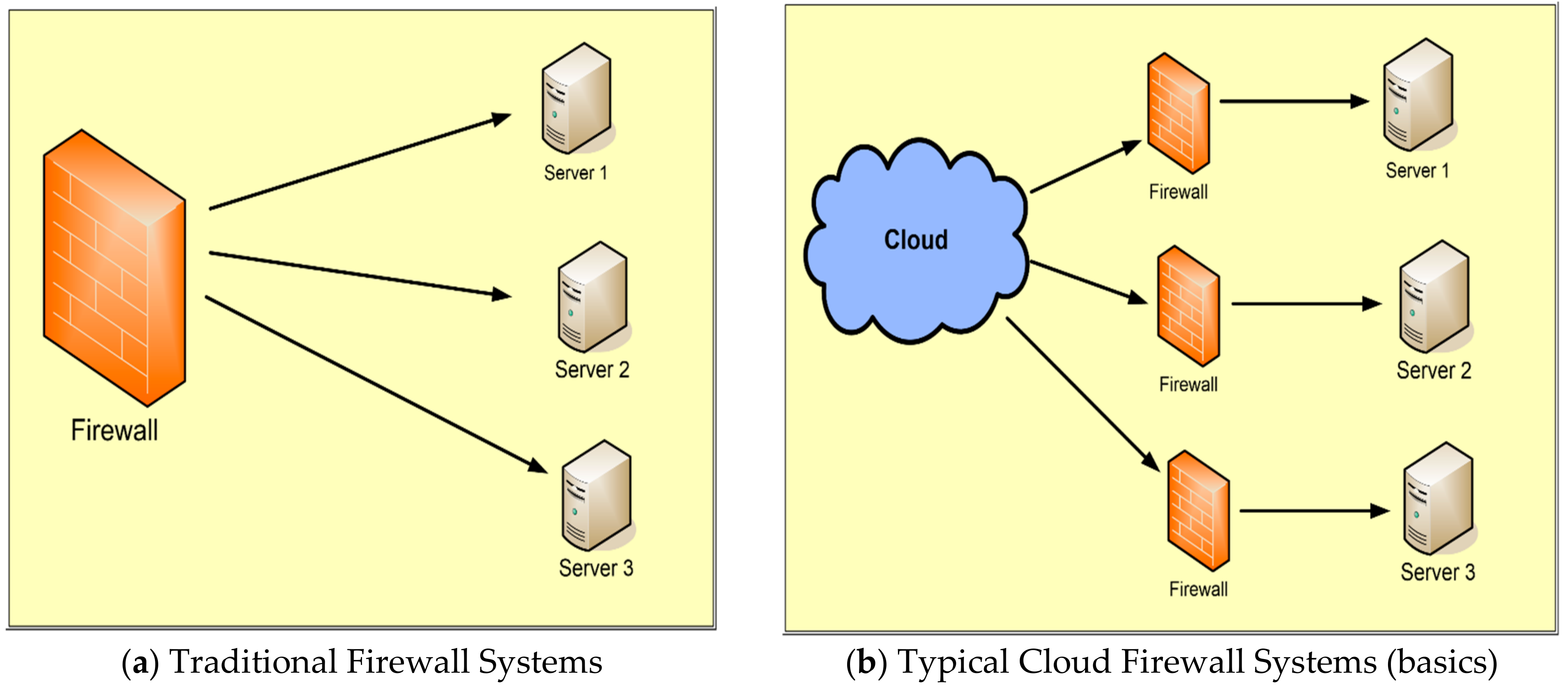
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
![]()
Telework And Mobile Security Guidance
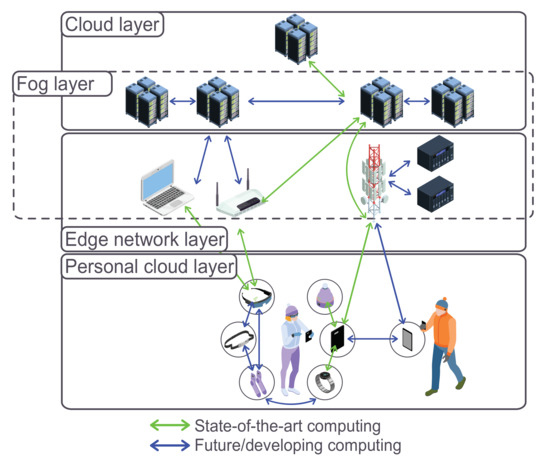
Sensors Free Full Text A Survey Of Security In Cloud Edge And Fog Computing Html
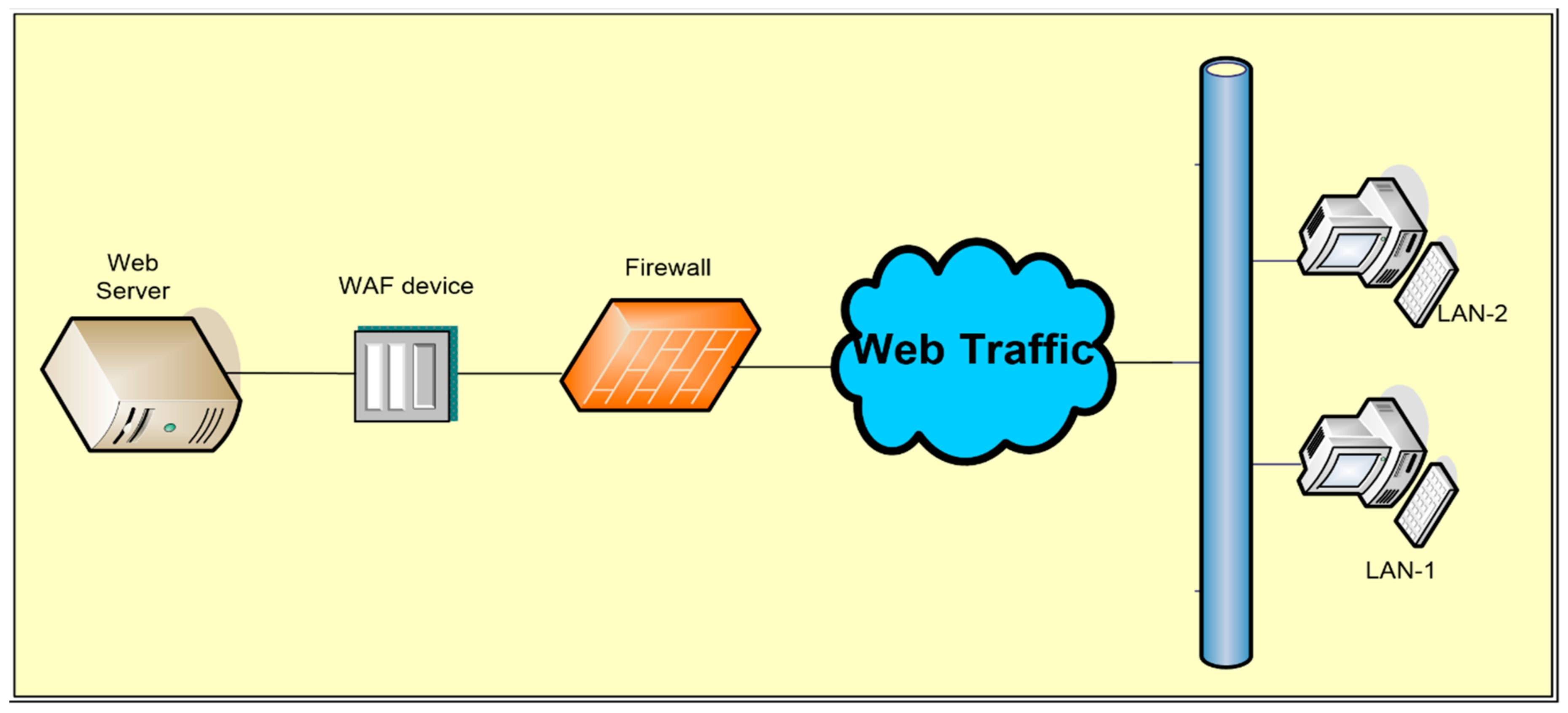
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

Build Secure And Manage Data Lakes With Aws Lake Formation Aws Big Data Blog
